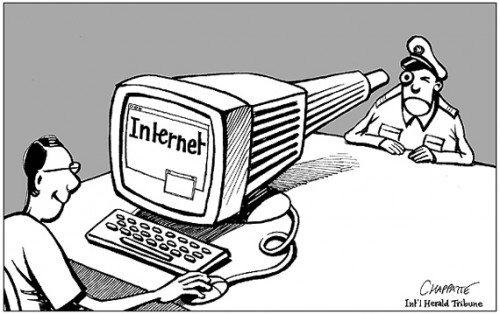
Last week the New York Times ran an article about some investigative work conducted by a researcher and student in the Toronto and Berkley universities. The two were investigating government use of surveillance software, and seem to have discovered evidence that many governments are using off the shelf software to spy on their own citizens.
And we are not talking about despot regimes here, the list of 25 countries includes Australia, Britain, Canada and the US. The chosen mode of dissemination is typical of virus or spyware spreading techniques, an email is sent to whoever is to be monitored, once opened the software is downloaded into the computer.
In Vietnam the system has been found running on Android phones, so I would say if they can do it in Vietnam they can do it elsewhere.
The alarm bells ring if you look at who is being targeted. In some cases political dissidents (as is the case in Ethiopia) receive the emails. Another worrying factor is where the spyware is sent from (IP addresses registered to Turkmenistan’s Ministry for Communication in one case).
The company manufacturing the program is British, and they state that they sell their product to governments to help them crack down on terrorism and organized crime, but the possibilities for abuse are obvious and also demonstrated.
One problem is that the sale of surveillance is largely unregulated. Commercially available software can remotely turn your webcam on and watch what you are doing, record Skype conversations, email exchanges, log keystrokes and look at images inside the machine, practically anything you would like to see you can. Useful maybe in a crime investigation, but a powerful tool in the wrong hands.
If you would like to ponder the matter of ethics in technological development and marketing more, I recently interviewed Chris Howard, CEO of online publisher LIBBOO. They have devised and patented a system of measuring how much influence an individual has upon a group, and which stimuli create and use that influence. In the interview I asked him about the responsibility he holds when his invention gets into the wrong hands, and you can read his response here on the Bassetti Foundation website.
I also have another post about other spyware and monitoring systems that are freely available on the Internet here, although they are toys in comparison to the system described above.
I have deliberately omitted all names above, but the New York Times article contains them all.