This is my two hundred and fiftieth (writing it out in full looks better than 250th) article on Technology Bloggers! It’s taken nearly four and a quarter years to get this far, but here I am, still blogging away. 🙂
That’s an average of 5 posts per month!
Not that anyone’s keeping score, but Jonny is hot on my heals now with 165 – just 85 behind me!
Finally, wireless charging on a mainstream mobile phone has arrived. Samsung’s Galaxy S6, S6 Edge and S6 Active all come wireless charging ready. Unfortunately we aren’t yet at the stage where your phone can wirelessly charge in your pocket, you do have to buy a wireless charging pad and have it sit on that, but it’s a step further than we have ever been before. This article gives an incite into the technology behind wireless charging, and then in my next article I’m going to review Samsung’s official wireless charging pad.
Wireless Charging Technology
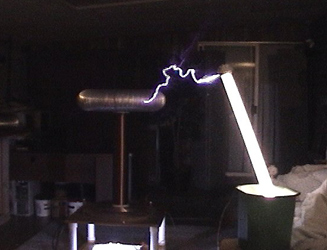
The capability to power things wirelessly is not a new phenomenon. Way back in the late 1800s, Nikola Tesla was using his Tesla Coil to power things from across the room. You might have done a similar experiment in science lessons at school, using a Tesla Coil to light up a light bulb.
The reason it’s taken so long for wireless charging to become mass market is because compared to wired charging, it is hugely inefficient. Wireless charging wastes a lot of energy as heat, meaning less is used to actually power the device. Wireless charging also takes longer than wired power, and as such is much more expensive.
Plugging my phone (the Galaxy S6) into a standard micro USB port will charge it from flat in around 2 hours. Plugging it into a fast charger takes just over an hour for a full charge. Charging wirelessly from flat takes over 3 hours. That’s 3 hours of electricity being used, compared to 1 in a fast charger.
Wireless charging has also taken a while to become mainstream because of problems with proximity. Tesla could power a light bulb from across the room, but that wasn’t controllable. If he had 2 light bulbs and only wanted to power one, he had no way of stopping power reaching the other. With so many different devices and radio frequencies about today, it is essential that wireless charging works without interfering with any other signals – for example your mobiles 4G signal. As such wireless charging has a very low proximity range. My S6 quite literally has to be on or within an inch or two of the pad to charge. A range of 1 meter would be fantastic, however that could fry other bits of tech, or ruin the magnetic strip on my credit cards.
Despite over 100 years in the making, wireless charging is still in reasonable early stages of development. It is a great idea, and when it works, it is super convenient and very useful, but still has a long way to go.
If you want to find out more about how wireless charging works, I recommend this YouTube video as a good place to start.